Tech Tips
Pat Nudo, Computer Network Engineer
Tips:
- AVAYA Phone Information
- Cyber Security (PDF)
- Avoid Email Hoaxes
- Gone Phishing
- Do Not Spam
- Avoid Viruses
- Reduce Spam
- Internet Speed
If you have any questions or concerns regarding technical issues with your work computer, contact us.
Gone Phishing!
What is Phishing?
Phishing attacks use both social engineering and technical subterfuge to steal consumers' personal identity data and financial account credentials. Social-engineering schemes use 'spoofed' e-mails to lead consumers to counterfeit websites designed to trick recipients into divulging financial data such as credit card numbers, account usernames, passwords and social security numbers. Hijacking brand names of banks, e-retailers and credit card companies, phishers often convince recipients to respond. Technical subterfuge schemes plant malware onto PCs to steal credentials directly, often using Trojan keylogger spyware. Pharming malware misdirects users to fraudulent sites or proxy servers, typically through DNS hijacking or poisoning.
How to Avoid Phishing (and Pharming) Scams
The number and sophistication of phishing scams sent out to consumers is continuing to increase dramatically. While online banking and e-commerce is very safe, as a general rule you should be careful about giving out your personal financial information over the Internet. The Anti-Phishing Working Group has compiled a list of recommendations below that you can use to avoid becoming a victim of these scams.
Newer Spear Phishing, targeted attacks, are not only personalized (they seem to know you, address you by name), but also seem to come from authoritative or trusted sources. Recently a Spear Phishing attack on the Department of Energy resulted in over a gigabyte of sensitive data being stolen.
- Be suspicious of any email with urgent requests for personal financial information
- unless the email is digitally signed, you can't be sure it wasn't forged or 'spoofed'
- phishers typically include upsetting or exciting (but false) statements in their emails to get people to react immediately
- they typically ask for information such as user names, passwords, credit card numbers, social security numbers, etc.
- phisher emails are typically NOT personalized, while valid messages from your bank or e-commerce company generally are
- spear phishing emails are personalized, and seem to come from authoritative or trusted sources
- Don't use the links in an email to get to any web page, if you suspect the message might not be authentic
- instead, call the company on the telephone, or log onto the website directly by typing in the Web address in your browser
- Avoid filling out forms in email messages that ask for personal financial information
- you should only communicate information such as credit card numbers or account information via a secure website or the telephone
- Always ensure that you're using a secure website when submitting credit card or other sensitive information via your Web browser, and check the site's certificate credentials to make sure it belongs to a trusted entity
- to make sure you're on a secure Web server, check the beginning of the Web address in your browsers address bar - it should be "https://" rather than just "http://"
- Consider using a third party DNS provider, such as Quad9 DNS or OpenDNS, to help prevent DNS Spoofing or DNS Poisoning (this may not be an option in some settings, such as at work).
- Consider installing a Web browser apps or extension to help protect you from known phishing fraud websites, here are some to choose from:
- The newer versions of the more popular browsers now have some built in ability to try to warn you about fraudulent sites, make sure they are enabled
- FireFox's WOT (Web Of Trust) add-on extension warns you about risky websites that try to scam visitors, deliver malware or send spam.
- FireFox's Certificate Patrol add-on extension warns you if an SSL license on a web site looks fraudulent or has changed since the last time you were on there, this can help you determine if the site is real.
- Regularly log into your online accounts
- don't leave it for as long as a month before you check each account
- Utilize multi-factor log in authentication when possible, this can be a powerful way to protect your online accounts
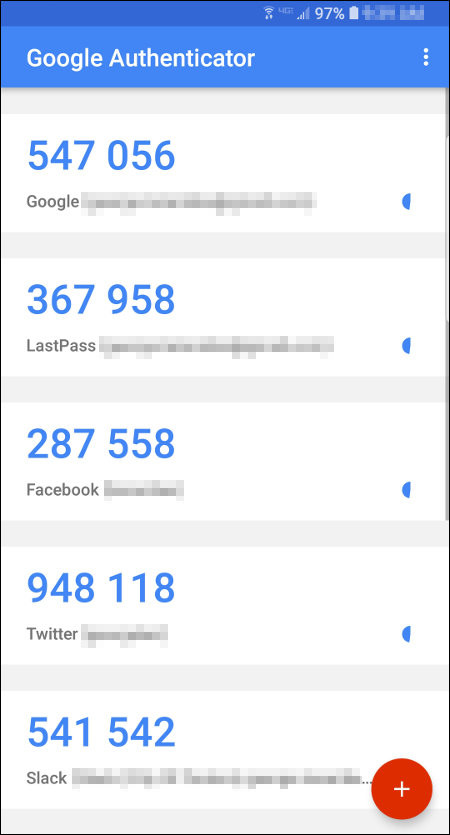 many sites now offer the ability to use an app, such as Google Authenticator, on your smart phone, it gives a code that you use to log into your account, the code changes about twice a minute
many sites now offer the ability to use an app, such as Google Authenticator, on your smart phone, it gives a code that you use to log into your account, the code changes about twice a minute- many sites now offer the ability to register your cell phone with them so they can send you security codes that you will echo back to their web site while logging in
- some other sites have you print out a card with codes on it that they then ask you to enter while logging in
- Regularly check your bank, credit and debit card statements to ensure that all transactions are legitimate
- if anything is suspicious, contact your bank and all card issuers
- Ensure that your browser is up to date and security patches applied
- Always report "phishing" or "spoofed" e-mails to the following groups:
- forward the email to
- forward the email to the Federal Trade Commission at
- forward the email to the "abuse" email address at the company that is being spoofed (e.g. "")
- when forwarding spoofed messages, always include the entire original email with its original header information intact
- notify the Internet Fraud Complaint Center of the FBI by filing a complaint on their website: www.ifccfbi.gov
For more information, check some of the following sources:
For more information about how to protect yourself, see our Fact Sheet 17a Identity Theft: What to do if It Happens to You at www.privacyrights.org/fs/fs17a.htm.
Read the information and tips put out by the Federal Trade Commission about phishing at www.ftc.gov/bcp/conline/pubs/alerts/phishingalrt.htm.
Read the Department of Justice's recent whitepaper "Special Report on Phishing" in PDF format at www.antiphishing.org/DOJ_Special_Report_On_Phishing_Mar04.pdf.

![[opens in new window] [opens in new window]](../images/leavesite.gif)